In this blog, I will share an overview of networking basics so that you can get one step closer to becoming a cybersecurity professional! I will explain the basic topics I mentioned in this blog in greater depth.
Table of Contents
ToggleCONTENT
-
- IP Address Types
-
- Network Address Translation (NAT)
-
- Subnetting
-
- TCP Protocol in Depth
-
- UDP Protocol in Depth
IP Address Types
Internet Protocol Version 4 (IPv4)
IPv4 is the version of IP address that most people are familiar with today. It is 4 bytes long, with each byte being separated by a dot (like 192.128.0.5) and containing 8 bits. This IP address is converted to binary and since there are 32 bits of data, there is a total of 4,294,967,296 (232) possible addresses . Even though that is a large number of possible addresses, there is a problem with this version of IP address. When it originally came out, nobody had anticipated that computers would have become as prominent as they are today. Nobody had ever thought that 4 bytes would not be enough, but it is a problem we continue to face today. People saw this problem coming from a while ago and needed to find a way to fix it.
Network Address Translation
One way we have tried to delay the IP address issue is through the use of the Network Address Translation. If you remember from the previous level of this series, I mentioned the difference between private and public IP addresses and how NAT was used to distinguish them. Because of the NAT, people from different networks could share the same private IP addresses without facing any conflicts within their respective networks. However, to interact with each other across the internet, they would need to transmit the data using the network’s shared public IP address. The creation of public and private IP addresses proved to be an excellent solution as it allowed multiple computers in a network to share an IP address whilst being able to freely communicate within their network and across the internet. It worked so well that when a new version of IP addresses came out, people stuck with IPv4 and NAT.
Internet Protocol Version 6 (IPv6)
The new version of IP addresses is 16 bytes long and contains 128 bits compared to the 32 bits of IPv4. However, this makes the IPv6 quite complicated and very long. This complication has contributed to the large resistance it has faced. Another reason people are reluctant to make the switch is the inevitable removal of NAT. Since there would be so many IP addresses (enough to give to each atom on the surface of the earth and more!), each device would be able to have their own public IP address. “How would this be a problem,” you might be wondering. Well, the use of private IP addresses acted as an imaginary firewall for the users. Since computers from other networks can only be accessed from their public IP address, the computers were unintentionally protected from the internet by NAT. but if it gets removed, all devices would be left exposed to the internet. The truth is IPv6 addresses will eventually be forced on everybody whether they prefer it or not.
Subnetting
A subnet is a way of splitting up a network in segments. An IP address consists of two parts: a network identifier and a host identifier. The network identifier identifies the network whilst the host identifier identifies the computer which is connected to that network. The issue is the length of each identifier can be variable. Subnet masks, however, tell us the length of each identifier.
Take 192.168.0.0 as an example, and let’s say that the subnet mask of this IP address is 255.0.0.0. That means the first byte (192.) is the network identifier whilst the last three are the host identifiers. Since the last 3 bytes are used for the host identifier, this LAN could technically have 224 (16,777,216) computers connected to it.
If you wanted to change the number of computers that can connect to your network, you would have to change the subnet mask. This leaves a trade-off between the number of hosts and number of networks.
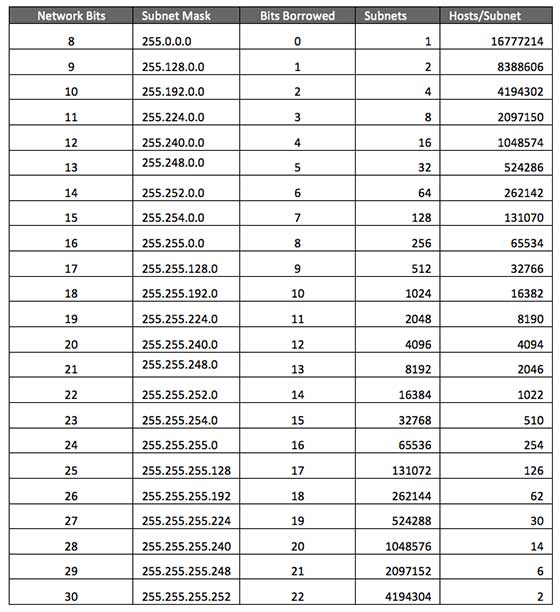
Classless Inter-Domain Routing (CIDR)
CIDR is simply a shorter way of displaying a subnet mask. Using the example above, instead of writing the subnet mask as 255.0.0.0, all you need to write is 192.168.0.0 /8 (because only the first byte, or first 8 bits were used as the network identifier).
TCP Protocol in Depth
In the previous level, I talked about how TCP prioritized reliable delivery of data over speed. In this level, I will specify just how it does this
TCP Handshake
The TCP handshake is used to setup a connection between two computers. Computer A, the one initiating the connection, sends a “SYN” (synchronise) flag to computer B. This packet contains a sequence number, which is randomly generated for security reasons, for our example, the sequence number will be 0.
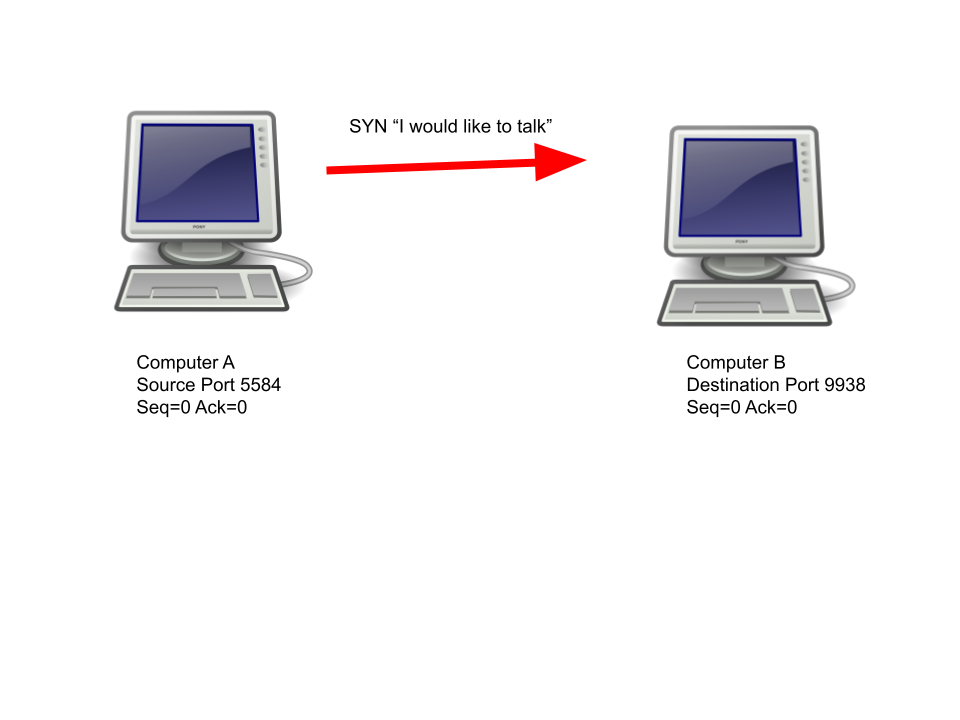
Computer B will then respond with “SYN” and “ACK” (acknowledge) flag. The packet will contain a new randomly generated sequence number as well as a new acknowledgement number, which is 1 digit higher than the random sequence number sent by computer A.
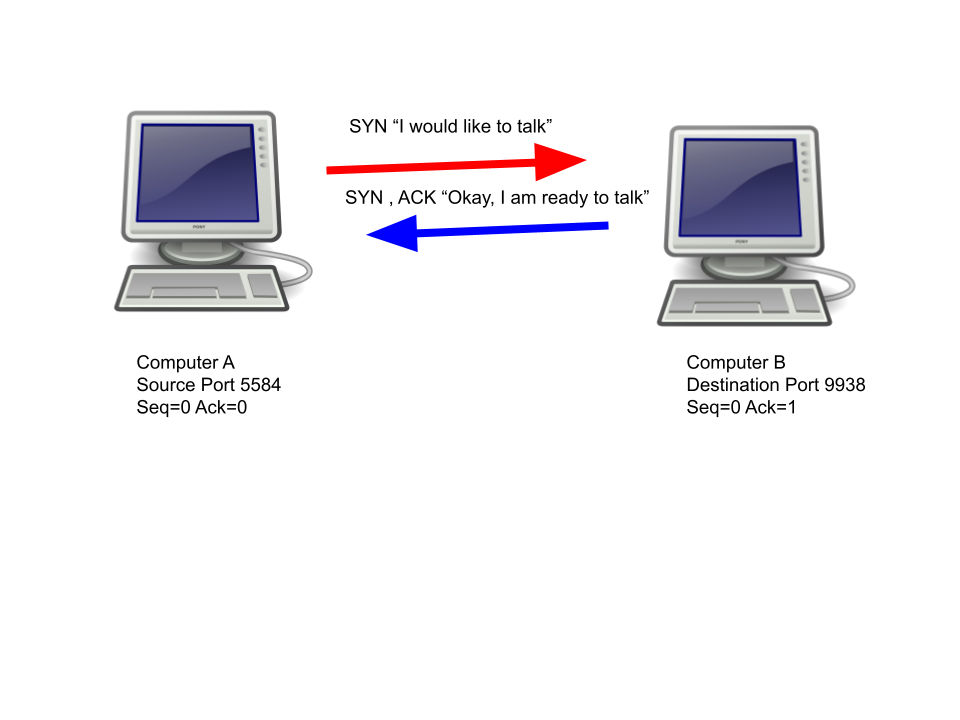
Computer A will then respond with an “ACK” flag and this flag will contain a sequence number which is 1 digit higher than the acknowledgement number generated by computer B.
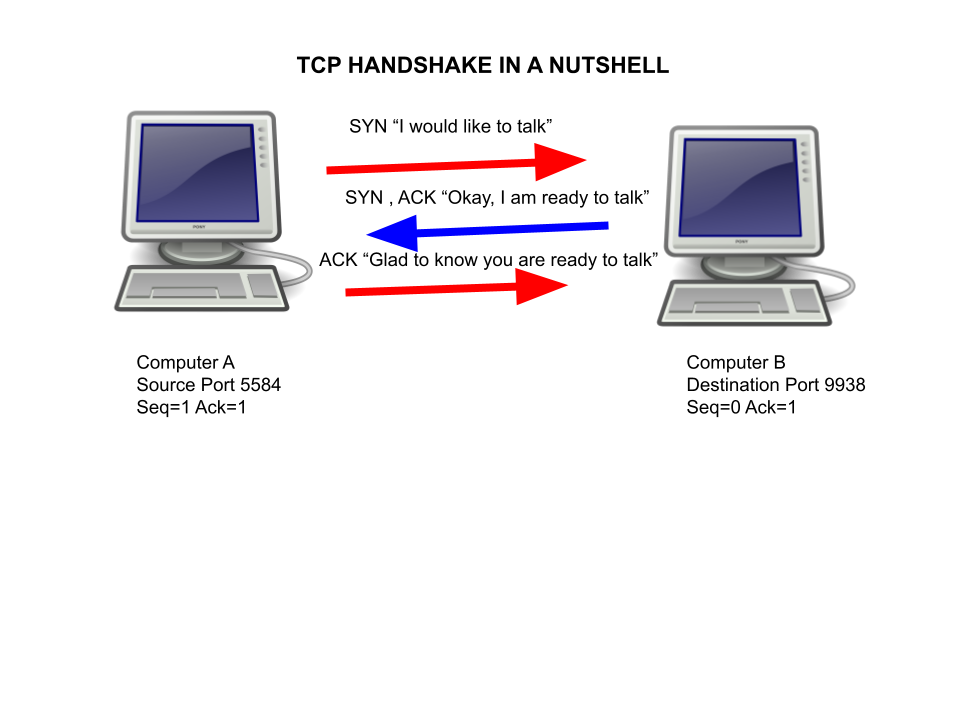
Now that the handshake is complete, the two computers are able to send data to each other. Additionally, both computers can check if any data was lost-in-transit by monitoring the sequence and acknowledgement numbers (more on this below).
TCP Transmission
| Source | Destination | Info |
| Computer A | Computer B | 3230 -> 6411 [PSH, ACK] Seq=1 Ack=1 Len=6 [Data=Hello] |
| Computer B | Computer A | 6411 -> 3230 [ACK] Seq=1 Ack=7 Len=0 |
Notice how the acknowledgement number jumps from 1 to 7. That is the acknowledgement number is incremented by the length of the packet. This is to ensure that all contents of the data packet are received. For example, If the length of a packet is 48 but the acknowledgement number is only incremented by 23 digits, then Computer A will know it lost some data in-transit. Even though the length is 0 of the flags being sent during the handshake and teardown, the sequence and acknowledgement numbers get incremented by 1 so that the other computer knows it received the flag.
TCP Teardown
When the two computers are finally ready to stop sending data to each other, the TCP Teardown process begins. First, the computer that wants to destroy the connection sends a “fin” packet (finish) with the current sequence number.
Computer B will then respond with an “ACK” packet which will contain a sequence number and an acknowledgement number which is computer A’s sequence number higher by 1 digit. After that, computer B will send its own FIN , ACK flags to let computer A know it is ready to end the connection. The packet will contain the same numbers from computer B’s original “ACK” packet.
Lastly, computer A will end the connection with a final “ACK” flag. This packet will contain an acknowledgement number which is computer B’s sequence number increased by 1.
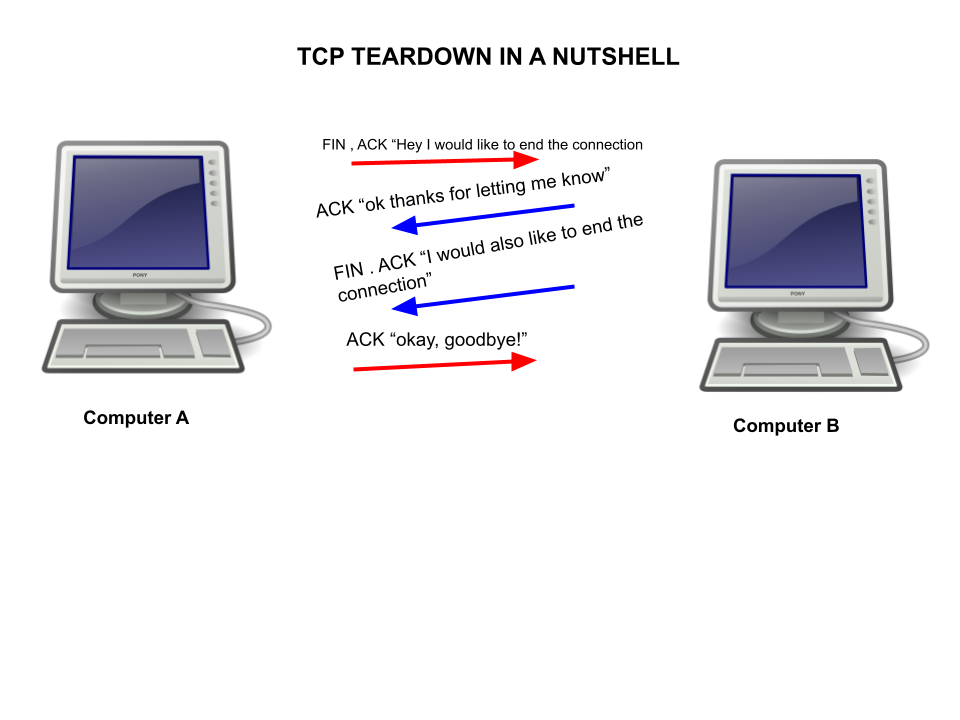
As you can tell, the process for computer A to send information to computer B through the TCP protocol is quite a long one. Despite this, it does guarantee a reliable transmission of data from one computer to another due to the sequence and acknowledgement numbers.
UDP PROTOCOL IN DEPTH
If you managed to stick through the complexity of data transmission in the TCP protocol, you’ll be relieved to know that the UDP protocol only contains one step: sending the data. The UDP protocol does not have any handshake or teardown steps like the TCP protocol does.
That means if the data never reaches computer B from computer A, neither one of them will know as computer A believes it sent the packet and computer B never knew there was a packet coming in the first place.
The simplicity of UDP is what makes it so much faster than the TCP Protocol.So, even though that makes it a lot less reliable, it can provide a better experience when a client is using a real-time application such as a voice chat or video call. Imagine how frustrating it would be if your call paused each time a packet was lost-in-transit!



