Whether you are looking to brush up on your computer networking skills, aiming to become a network administrator, or gain an advantage in this year’s CyberPatriot competition, Cisco packet tracer is a free network simulation tool that will provide you vital hands-on experience. Throughout these next few weeks, I will be posting many blogs related to this tool in order to share some of the things I have learned from using it! If you are new to my website, check out this blog to learn about navigation through the cisco IOS and the different modes of configuration. In this blog, I will specifically be going over the protocols that allow for network components to interact with each other!
Communication Fundamentals
Networks can vary in shape, size, and function. People exchange many ideas using different communication methods. However, there are three elements which all communication methods have:
Channel- The media over which the message travels from the source to the destination.
Message Source/ Sender – The device or individual who is sending a message to another device or individual
Message destination / Recipient – The device or individual who is receiving the message.
Network Protocol Requirements
In order to deliver a message that can be understood by the receiver, protocols must:
- have an Identified sender and receiver
- Contain a common language
- maintain good timing of delivery
- Include confirmation of delivery status
Network Protocol Types:
- Network Communications Protocols: These protocols enable two or more devices to communication with each other in one or more networks. Examples of these protocols are HyperText Transfer Protocol (HTTP) and Transmission Control Protocol (TCP).
- Network Security Protocols: These protocols secure data to ensure authentication, data integrity, and data encryption. Some examples of these protocols include: Secure Shell (SSH), Secure Sockets Layer (SSL), and Transport Layer Security (TLS).
- Routing Protocols: These protocols are used in order to find the best path for data packets to travel. Examples of these protocols include: Open Shortest Path First (OSPF) and Broad Gateway Protocol (BGP).
- Service Discovery Protocols: These protocols automatically detect devices and services and make the process of adding new devices to a network much more convenient. Examples of these protocols include Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS), which is used for converting IP addresses into domain names.
Protocol Suites
In order for network communications to work as efficiently as possible, protocols need to be able to work together seamlessly. Protocol suites are exactly that: a group of related protocols necessary to perform a communication function. Think of it like communicating with a stranger. If we all spoke different languages and used unique methods of communication, nobody would be able to interact with each other!
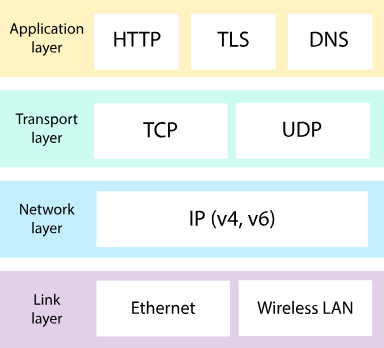
Photo by Khan Academy
Evolution of Protocol Suites
TCP/IP or Internet Protocol – This protocol is maintained by the Internet Engineering Task Force (IETF) and is the most prevalent protocol today.
Open Systems Interconnections (OSI) protocols – More commonly known for its OSI Model, the OSI protocols were developed collectively by the International Organization for Standardization (ISO) and the International Telecommunications Union (ITU). These protocols have largely been replaced by TCP/IP.
AppleTalk – A short-lived protocol suite launched by Apple Inc. in 1985. Apple replaced AppleTalk with TCP/IP in 1995.
TCP/IP Protocol Example
The Internet Protocols are available in three layers: application, transport, and Internet. The application layer’s primary job is to provide direct methods for the user to send and receive data over the internet. The transport layer is responsible for enabling communication between two hosts in order to send the data packages. The internet layer segments the data packages into packets and routes to the path for their destination host. The network access layer does not contain any TCP/IP protocols, however, it uses LAN protocols such as Ethernet and Wireless LAN (WLAN) to physically transmit the IP Packets to the designated host.


