In this blog, I plan to share an overview of networking basics so that you can get one step closer to becoming a cybersecurity professional! This is the most basic level of the topic, where I will give a brief overview of the inner workings of a network!
Network Topologies
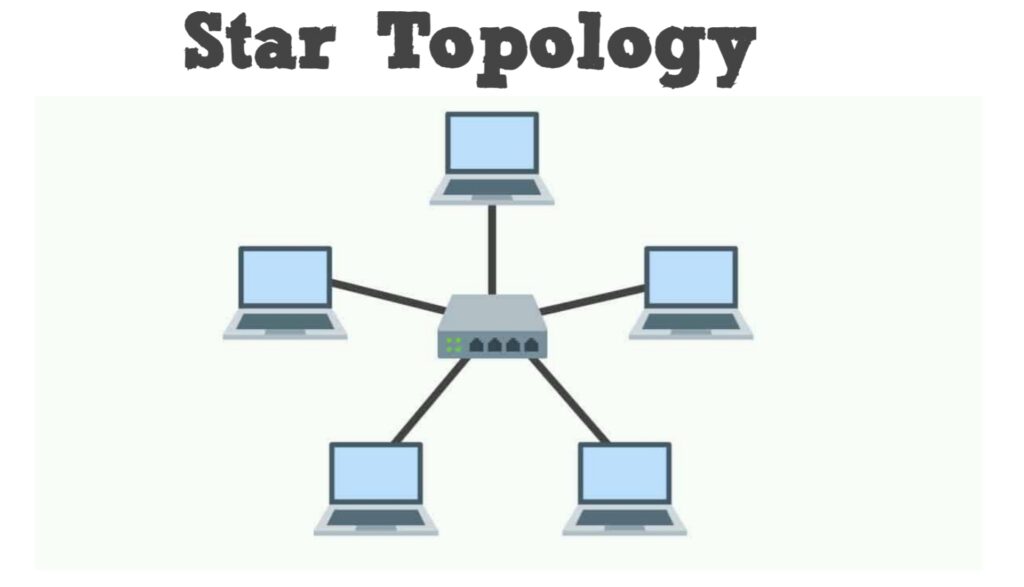
A network topology is simply the shape physical layout of the network. The most common type of network topology is the start topology. The star topology contains a central point which all devices on the network connect to. This topology is very effective because even if one device fails, the rest of the devices remain unaffected (unless the affected device happens to be the central point).
Network Hardware
Switches
A switch is a device which connects computers on a network together. It is a device which sits in the middle of a star topology network. It can be connected to many different devices at once. Additionally, it decides which cable the data should be sent to based on which computer it is meant for.

Hubs
Similar to switches, hubs connect computers on a network together. However, what makes hubs different is they are unable to identify where the data it’s given is meant to be transmitted. Therefore, instead of giving the data to one computer, it sends it to all of them. The computer which the data was meant for will accept it whilst the other devices discard it. Hubs are an older model of the switch, but they are still commonplace in the form of wireless access points. Since the wireless access points broadcast the data through radio waves, it is not possible for them to transmit data to a specific device at once.

Routers
A router is a device which connects two networks together. Typically, it is used to connect a LAN (local area network, such as a school or office) to the internet, but it can connect any two networks. It decides which pieces of data need to go to which network. Most modern routers have the same functionality as switches, but if more ports are needed, a switch can be plugged into the port of a router.

NIC
A NIC , also known as a network interface card, allows a computer to interface with a network. These NICs can be wired or wireless. A wireless NIC uses an antenna to communicate through radio waves on a Wi-Fi connection. A wired NIC on an input jack and a wired LAN technology (most commonly an ethernet cable). Wired NIC can also be connected through USBs. Additionally, wired NICs are typically much faster than wireless ones because the ethernet cables directly connect your device to the router.
MAC Addresses
A MAC address, or Media Access Control address, is an address given to a NIC when it is produced. Each NIC is meant to have its own unique MAC address. MAC addresses are used to identify a computer on a local network and allow switches to know which device to give data to. They are used alongside a private IP address, however, MAC addresses never change.
Mac Address example: 00:2B:46:11:3A:B5
IP Addresses
An IP address helps identify your computer on the network and enables other local computers to find your device . There are two types of IP addresses: public and private (also called internal and external).
Private Addresses
A private IP address is one assigned to your computer on the LAN. The address is selected by a router and has a small set range of possible addresses. This IP address cannot be accessed by other computers from a different LAN. This address is used to communicate with other computers in the internal network. Additionally, two computers in the same LAN cannot possess the same private IP address otherwise internet connection issues will arise.
Public Addresses
A public IP address is shared by all computers in a LAN and is internet facing. They are used to communicate over the public internet. It is provided by your internet service provider. It can be any set of numbers which are not contained in the range set for the private IP addresses. The ability to share an IP address is handled by the NAT (Network Address Translation), which is discussed in further detail in this level of the series.
The main reason behind using private and public IP addresses is that there simply aren’t enough IPv4 addresses for each individual device to have a unique address. Therefore, allowing multiple devices to share an IP address in a LAN requires less addresses to be used up. Furthermore, the use of private area networks allows for further protection for the internal networks as their IP addresses are not accessible to the public internet.
Packets
Data Packets are a unit of data that can be transmitted over a network. Data is cut into packets before being sent out. Not only do they contain the data, but also the destination IP address and MAC address. They are very similar to a letter. Each envelope contains a paper letter as well as the destination address. These data packets tend to be quite small. Their size is dependent on a few factors such as which protocol is being used.
Protocols
Protocols are a set of rules which determine how two or more parties interact. These protocols define the format of the data and check if it was transmitted successfully. The two protocols I will focus on in this blog are TCP and UDP.
TCP
The TCP (Transmission Control Protocol) is a protocol designed to provide reliable delivery of data packets throughout the internet. This protocol utilizes the TCP Handshake to prepare two computers to interact with each other. After the data is transmitted, the connection between the two computers is closed by the TCP teardown. Additionally, the TCP has extra measures to retransmit any data that was lost in transit. Despite the reliability of the TCP, it is quite slow to transmit data.
UDP
The UDP (User Datagram Protocol) is much more focused on speed rather than reliability. It does not require a handshake, check data lost-in-transit, or check data corruption. It is mainly used in voice chats, online video games, and any other application where speed is more important than reliability. After all, what difference would it make for the user if a single frame is lost in transit when trying to watch a video?
TCP – Reliability
UDP – Speed




Pingback: What Happens When You Send an Email?
Pingback: How Protocols work in a Network - Salem Cybersecurity