Before a penetration tester learns how to exploit into a system, they must learn what vulnerabilities are available. Therefore, if you are looking to become a top penetration tester, it is crucial for you to know the ten most common web security vulnerabilities. This blog will contain information on each of the ten vulnerabilities and how they occur. If you would like to learn more about the OWASP Top 10 check out this amazing room made by TryHackMe or this article written by OWASP themselves.
1. Broken Access Control
Websites contain information that is not meant to be seen or modified by website visitors, so when a visitor is able to break the access control, it puts a company at risk of a data breach or system compromise. This vulnerability jumped from fifth to the first most common vulnerability in web applications in 2021. According to OWASP, 94% of applications were found with some sort of broken access control!
Insecure Direct Object Reference
IDOR occurs when a user is able to expose a Direct Object Reference (such as a user ID). This vulnerability would allow users to access specific objects on a website that they originally weren’t supposed to access. For example, if a URL to my bank account was https://Fakebank.money/account?id=222, all of my information would be contained on that page. However, a huge issue may arise if a user is able to gain their ID from 32 to 222. Now, instead of looking at their bank information, they have access to all of mine!
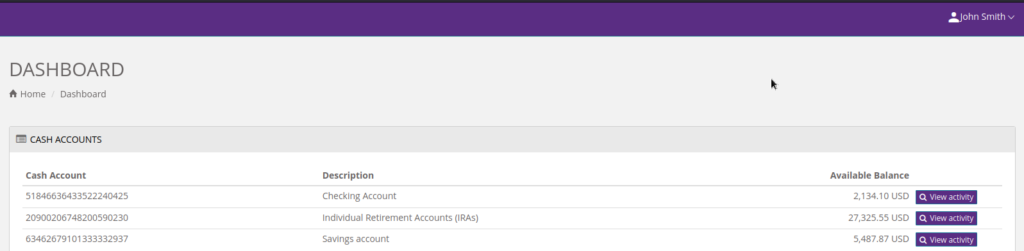
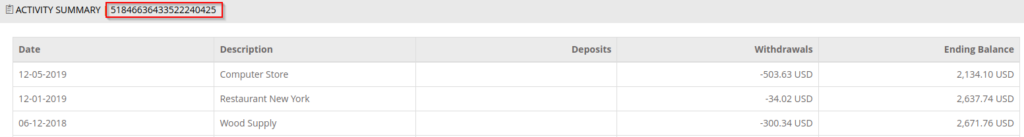
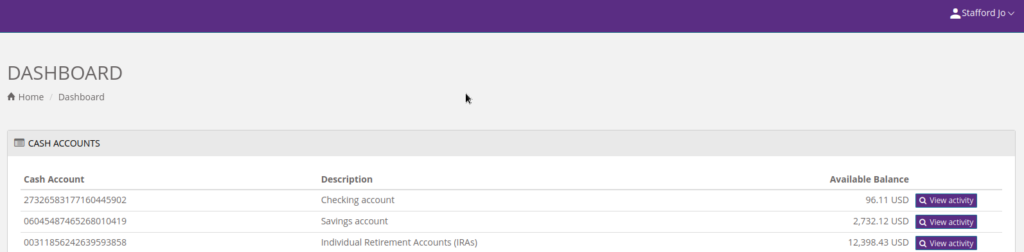

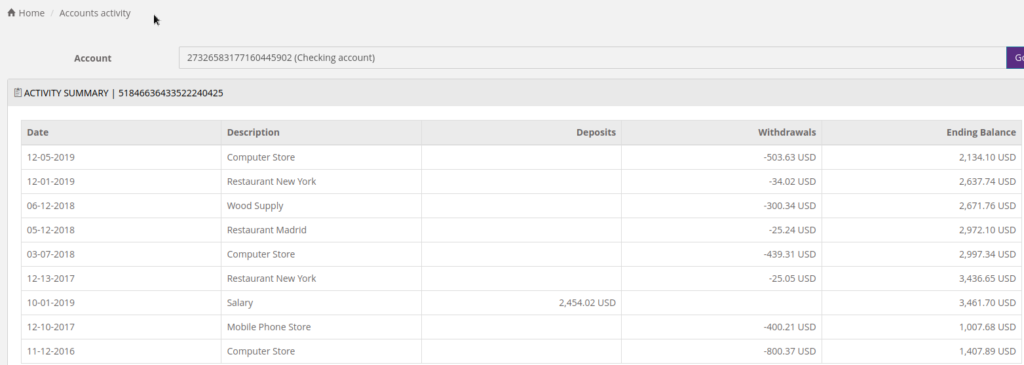
If you would like to try this exploit yourself, check out this video for a walkthrough of this exploit!
2. Cryptographic Failures
Before I explain what cryptographic failures are, you need to understand what a secure web application does to protect a user’s data:
- First, it is essential that the communications that occur between a user and the server are encrypted. That way, no eavesdropping can happen while the data is being sent. This is called encrypting data in transit.
- However, it is equally as important for information to be kept secure in the servers they are stored in. If emails are left unencrypted in a server managed by an email provider, those emails can be read by the provider. This form of encryption is called encrypting data at rest.
A cryptographic failure occurs when an organization does not handle certain information properly. For example, storing sensitive information in an insecure database can leave it exposed to cyber criminals. Insecure databases are vulnerable to SQL injections, don’t implement hashed and salted passwords, and/or use a weak cryptographic key.
Facebook’s Cryptographic failure
In 2019, it was revealed that upwards of 540 million records related to Facebook users were unintentionally leaked by two third-party Facebook app developers. Records such as photos, Facebook usernames, passwords, and IDs were left completely unencrypted on Amazon’s cloud service.
If this vulnerability interests you, check out this article which goes into further depth about how cryptographic failures occur and even how to prevent them.
3. Injection
Injection flaws typically occur because the application misinterprets user input as a command or parameter. Two examples of injection attacks are:
- SQL injection: SQL injections occur when user input is passed to SQL queries. As a result, attackers can pass SQL queries to manipulate the outcome of the queries. These injections can potentially lead to attacks stealing sensitive information from databases, such as personal details and credentials.
- Command Injection: OS command injection is a vulnerability that allows attackers to execute arbitrary commands on the server that is running an application. When a function directly interacts with the server’s console, it gives the hacker endless possibilities such as listing files, reading their content, and running any commands they would like. If an application is not protected against this vulnerability, they risk all of their data being compromised.
However, there are ways to prevent these injection attacks from occurring:
- Create a word whitelist: Only allow inputs that are found in a whitelist implemented by you. It is generally more secure to use a whitelist instead of a blacklist as a good hacker will be able to find an exploit around it.
- Stripping input: This method simply removes any input that contains dangerous characters before processing
4. Insecure Design
Insecure design refers to risks that arise due to a flaw in the architecture of the application. The application architecture is the roadmap for building the application; essentially the techniques and patterns used to design and build the application.
An example of an insecure design vulnerability is an insecure password reset. If a user were to forget their password, they would need to validate themselves using a code in order to change it. If an attacker wanted to brute-force their way into an account, they could brute-force the code. But, they’d be stopped after a certain number of tries due to rate limits. However, here comes the problem: What if the hacker used multiple different IP addresses to brute force the code? Now, the hacker is able to exploit the insecure design of the application as it doesn’t take this into account.
Since the application architecture deals with the early stages of the developmental process, it can require lots of changes to the application just to resolve it. The best way to avoid these vulnerabilities is to perform threat modeling at the early stages of development.
5. Security Misconfiguration
Security Misconfiguration issues occur when security could have been appropriately configured but wasn’t. Security misconfigurations include:
- Unnecessary features, privileges, and users
- Using HTTP (leads to cryptographic failure)
- Default Accounts with unchanged
What makes misconfigurations so dangerous is that they can occur in many locations in your environment such as the application stack, cloud services, and network layer.
Security Misconfiguration examples
- In 2015, Patreon was hacked because they had left a debug interface open for a Werkzeug console. Werkzeug, which can be accessed via URL, provides a Python console that will run code when you send it. This console allowed hackers to execute commands arbitrarily
- In 2021, Nissan had some leaked source code online. The reason behind the misconfiguration was discovered by a security researcher who claimed it occurred due to one of their Git servers using a default username and password (it was admin/admin, if you’re curious)
- A misconfiguration in the JIRA project management software exposed the sensitive data of hundreds of companies. The misconfiguration occurred due to the wrong permissions being assigned when creating filters in JIRA. The visibility of the filters was set to “All Users,” meaning anybody could have seen a company’s dashboard. The misconfiguration resulted in thousands of companies’ filters and dashboards being publicly exposed. These dashboards contained internal information such as employee names, current projects, and upcoming milestones.
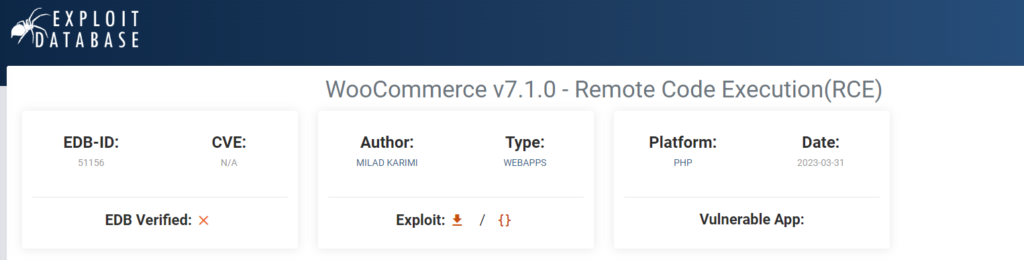
6. Vulnerable and Outdated Components
Sometimes, a penetration tester may find that a company they are testing is utilizing a program with well-known vulnerabilities. These vulnerabilities can be found on Exploit-db. This can be devastating for the company since the vulnerability is already well known and it takes the hacker minimal effort. For example, if a company used the WooCommerce plugin in order to sell things online, they could potentially be in harm’s way if they are using an outdated version of it. Make sure to always update your programs in order to avoid this vulnerability!
7. Identification and Authentication Failures
Authentication allows users to access applications by proving their identities. The most common form of authentication is the use of usernames and passwords. If a hacker is able to gain access to a user’s account, they could have access to some really sensitive data (depending on the application, of course). Therefore, it is crucial for companies to put strong password policies in place so they can avoid:
Brute-force attacks: An attacker may be able to launch a brute-force attack in order to obtain a user’s password
Guessing Weak Passwords: If a company uses a weak password policy, it may leave their users vulnerable, especially if they have easy-to-guess passwords such as “qwerty123.”
There are a few ways to avoid authentication vulnerabilities:
Using a strong password policy: If users are required to create a strong password, it makes the hacker’s job a lot harder as they would be unable to guess the user’s password
Attempt Timeouts: If a user reaches a certain number of attempts in a specified amount of time, they should be timed out in order to prevent brute-force attacks from occurring. For example, implement a feature that times out a user for ten minutes if they incorrectly type their password ten times in 30 seconds.
8. Software and Data Integrity Failures
Integrity in cybersecurity is essential: it is the ability to ensure that the data we transmit remains unmodified. If data is open to modifications, that leaves room for cyber criminals to add unwanted or malicious code to that data. Therefore, it is very important for companies to add integrity checks whilst dealing with their customer’s data.
For example, to prove that a file was untampered, companies will add hashes alongside a file. If the file’s content changes even slightly, the hash will be completely different from the original.
This sort of vulnerability occurs when companies do not implement any sort of integrity checks, leaving an opportunity for cyber criminals to manipulate their data.
9. Security Logging and Monitoring Failures
Security logging and monitoring allow companies to detect potential threats. System administrators can spot these potential threats by interpreting the data and finding unusual patterns. For example, if the administrator notices requests from a random location across the world, that should be a red flag they further inspect. If the logging mechanism fails or isn’t even being maintained in the first place, there is no opportunity for security analysis. Attackers can continue to attack a company’s system without being easily identifiable to the logging failure. Additionally, even if the company is able to find a threat, its evidence would be missing the useful information that logging provides.
Ensuring that all requests in a network –especially login attempts– are adequately logged is a significant first step for a company to ensure they are able to identify attackers.
10. Server-Side Request FORGERY (SSRF)
SSRF attacks enable threat actors to make a company’s application behave in unintended ways. Attackers are able to manipulate the application into making requests into unwanted and likely malicious applications. The attacker is able to make this request even through a firewall and VPN. A successful SSRF attack can result in unauthorized access to data within an organization, and potentially even the ability to perform arbitrary commands.
Example SSRF Scenarios
- Collecting sensitive data using local files such as /etc/passwd
- Access Metadata of cloud services
- Launching Denial of Service Attacks
THM SSRF Example
This vulnerability may seem confusing, so here is an additional example I found in TryHackMe’s OWASP Top 10 room:

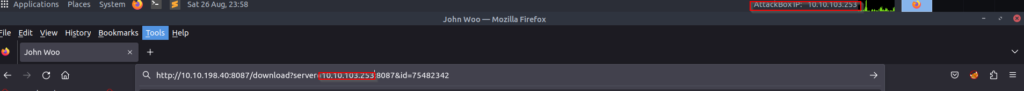
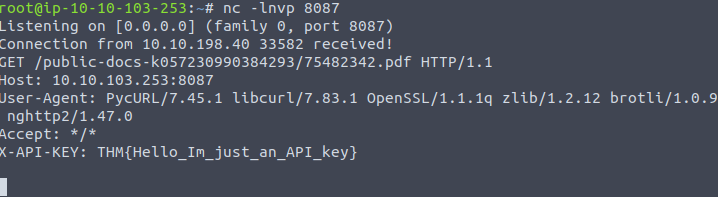
I replaced the secure-file-storage.com with the IP address I was using for my THM AttackBox.
nc -lnvp 8087Lastly, I am able to obtain the API key using Netcat!
Conclusion
Thank you for making it to the end of this blog! It is important for any cybersecurity expert to be fully aware of the OWASP Top 10, whether they are part of the blue, red, or purple team. Keep in mind that these ten vulnerabilities change over time, so it is important to continuously keep yourself up to date with the most common vulnerabilities.



